blog
Benefits of using a VPN

blog
How real is AI?
blog
What is Single Sign-On and who is it for?
blog
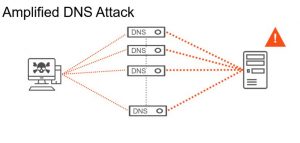
DDoS: It’s not a matter of if, but when

blog
Risk and compliance management: Modernizing the cloud to address the realities of security and compliance
blog
Take a Fresh Look at Your IT Support Process
blog
How AI can shape the future of VoIP

blog
How surveillance is transforming these top six industries

blog
WiFi 6 powers real-world wireless enterprise applications
blog