
blog
Three Cyber Threat Hunting Myths
blog
The most pressing data concern in 2019
blog
Are EHRs useful?

blog
Why hybrid IT is the best of both worlds

blog
Going nowhere fast?

blog
Five common misconceptions about DDoS
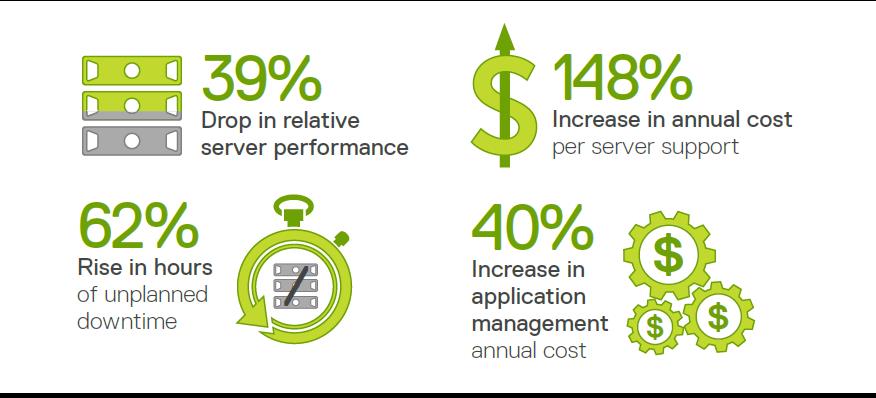
blog
Just Go Away! 4 Server Technologies to Ditch in 2019

blog
Why Business Leaders Should Care About Quantum Computing

blog
Top 10 Smart City Trends for 2019
blog