blog
4 virtualization types and their benefits
blog
Top security threats to financial services

blog
Data lake vs. data leak
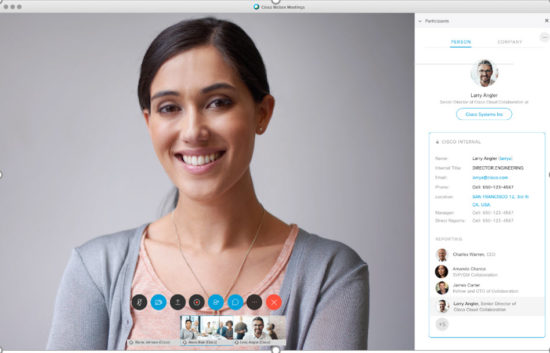
blog
Partner Post: 6 ways webex makes meetings experiences amazing

blog
The one-two punch of user and device trust
blog
Manufacturers concerned about PC shortage
blog
Quick facts about virtualization and the cloud
blog
How IT as a Service Solves the Everyday SMB Challenges
blog
It’s time to rethink your password
blog