blog
How to properly manage your fleet of VMs
blog
A closer look at fileless malware
blog
How can MSPs optimize healthcare?
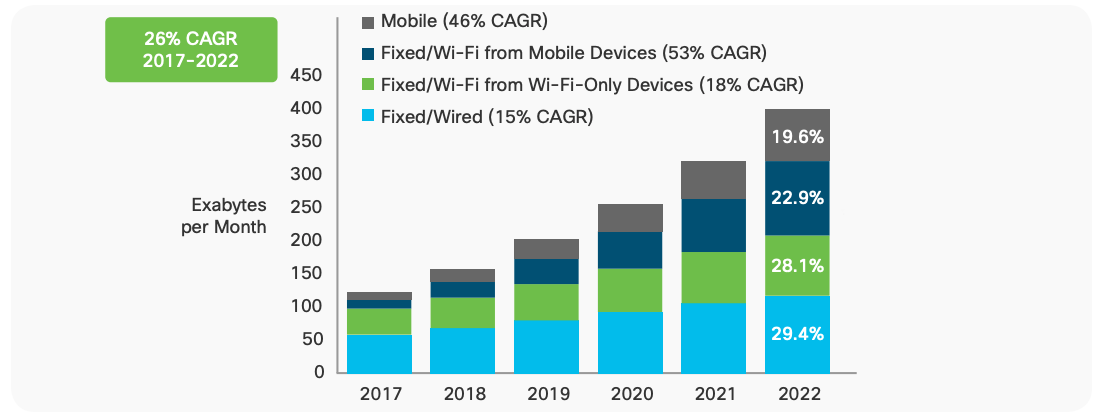
blog
Why WiFi 6 and 5G are different: Physics, economics, and human behavior
blog
Prolong laptop battery life with these tricks
blog
Do honest working hackers exist?

blog
A guide to maximizing your chances of success with IoT
blog
Why a technology business review is vital
blog
Cybersecurity for small- and medium-sized businesses
blog