blog
The Collateral Damage of DDoS Attacks - Part 1. What is what

blog
Seven Deadly Deceptions of Network Automation
blog
Data Capital: Separating the Winners and Losers of Tomorrow
blog
Humanity and Artificial Intelligence – Shape Our Future in Harmony, Rethink Our Societies.
blog
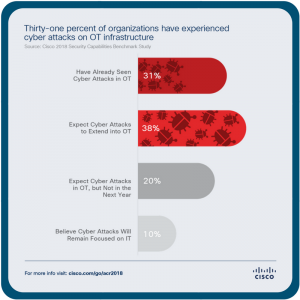
Attackers turn to IoT and ICS to find gaps in security
blog
The Fourth Network Revolution

blog
Is your Financial Service Firms defensive strategy stuck in the past?

blog
Using machine learning to detect possible insider threats
blog
Do You Know the Anatomy of a Ransomware Attack?
blog