Attackers turn to IoT and ICS to find gaps in security
Research from Cisco and partners reveal increased interest in IoT and ICS from security professionals and attackers alike
Technology solutions and processes that rely on the Internet of Things (IoT) are rapidly becoming standard equipment in many organizations as well as industrial facilities, thanks to IoT systems’ ability to automate and communicate with devices. Unfortunately, as we detail in the Cisco 2018 Annual Cybersecurity Report, attackers see benefits to IoT as well—namely, the ability to take control of IoT devices with weak or no security and build powerful IoT botnets. They also see value in taking control of operational technology (OT) systems, which are often used to manage critical infrastructure.
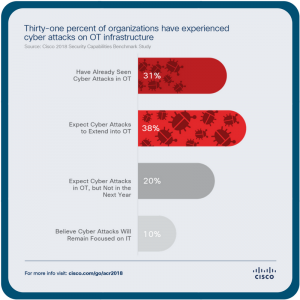
As presented in the report, research from the Cisco 2018 Security Capabilities Benchmark Study shows that many security professionals expect to see IoT and OT attacks in their networks. Thirty-one percent of security professionals surveyed said they’ve already seen cyber attacks within OT systems, while 38 percent said they expect that attacks will extend to their OT systems this year.
As one survey respondent said, “We still have OT devices that are 25 years old, and compressors and machines that are 40 years old. IT professionals are used to the schedule. [They say,] ‘Tell me when Windows X is no longer supported,’ or ‘Hey, this Oracle version is going EOL [end of life].’ There’s no such thing in the OT environment.”
 IoT botnets gain strength
IoT botnets gain strength
Research from Cisco partner Radware shows that massive IoT botnets such as Mirai, Brickerbot, and Hijami can be used to launch crippling attacks on networks. For example, application layer attacks are on the rise compared with network layer attacks—a shift, according to Radware, that can be attributed to growth in IoT botnets. The increase in application layer attacks is a concern because they have the potential to shut down large portions of the Internet.
Because IoT botnets are less resource-intensive than PC botnets to build and manage, attackers can invest more time and money in developing code and malware that can be used within the growing botnets. Operators of the Mirai botnet, which is known for advanced application attacks, are among those making investments in advanced attack methods.
Vulnerabilities in industrial control systems can place critical infrastructure at risk
The innovation and expertise that attackers are applying to IoT and OT is also spreading to industrial control systems (ICS), which connect electronic systems that are part of manufacturing and process control systems. In our new security report, researchers with Cisco partner TrapX Security share their recent investigations of attacks targeting ICS.
In one case examined by TrapX, attackers targeted ICS for a large international water treatment and waste processing company. The attackers used the company’s demilitarized zone (DMZ) to establish a foothold in the company’s internal network. They were able to accomplish this breach by taking advantage of server misconfigurations.
To reduce the risk of ICS breaches, TrapX offers advice for ensuring the integrity of industrial systems, such as reducing the use of USB memory sticks and DVD drives, and isolating ICS systems from IT networks. In addition, TrapX suggests creating policies that severely limit the use of ICS networks for anything but essential operations. Deployed together, these suggestions could reduce opportunities for attackers to gain access to critical systems.
“Leak paths” create opportunities for attackers
Devices that are connected to the Internet may also be at risk because of “leak paths,” discussed in the security report based on research from Cisco partner Lumeta. Leak paths are policy or segmentation violations or unauthorized or misconfigured connections created to the Internet on an enterprise network and allowing traffic to be forwarded to a location on the Internet, such as a malicious website.
Devices that don’t have permissions set up correctly, or are part of shadow IT efforts, are attractive to attackers using leak paths because they tend to be unmanaged and unpatched. According to Lumeta’s research, about 40 percent of the dynamic networks, endpoints, and cloud infrastructure in enterprises is leading to significant infrastructure blind spots and lack of real-time awareness for security teams.
Lumeta’s researchers believe that leak paths are on the rise, especially in cloud environments, where there is less network visibility and fewer security controls in place. To combat the leak-path problem, enterprises can implement segmentation policies to quickly determine whether unexpected communication between networks or devices is malicious.
Caution advised against IoT, OT, and ICS exposures
The strength of botnets—and the availability of leak paths, ICS vulnerabilities, and other weaknesses offering opportunities—speak to the need for greater attention on protecting IoT and OT systems. As the Security Capabilities Benchmark Study indicates, security professionals know the attacks are coming, which is a good reason to address security when devices are implemented, assess where IoT devices are on networks and what they can access. Moreover, a clear understanding of who’s responsible for securing connected devices is paramount. Attackers have identified clever ways to use IoT and ICS to their benefit. Now it’s up to defenders to devote more attention to this aspect of the threat landscape.
Published with permission from blogs.cisco.com
