blog
Five Reasons Mobile Devices Will Generate the Need for More Servers
blog
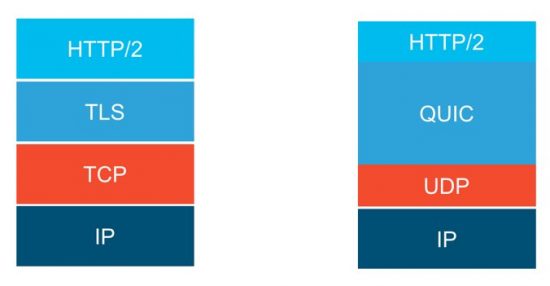
The Impact on Network Security Through Encrypted Protocols – QUIC

blog
What is the Difference Between a T1 and Comcast Coax? How to Find the Right Internet Connection for Your Business

blog
2 Factor Authentication: What it is and Why it's Critical for Your Business to Do Right Now

blog
The Cloud: Hosted Desktops

blog
The Cloud: WorkSurf

blog
The Cloud: Virtual Workspace

blog
The Cloud: Security & Compliance

blog