blog
Windows Exploitation and AntiExploitation Evolution

blog
Upstream Without a Paddle: What CIOs Need to Know About AI

blog
5 Things You Need to Know about Webex Meetings

blog
The Network Reliability Engineer's Manifesto

blog
Why a Big Data Approach is Key for APM

blog
VPNFilter: a global threat beyond routers
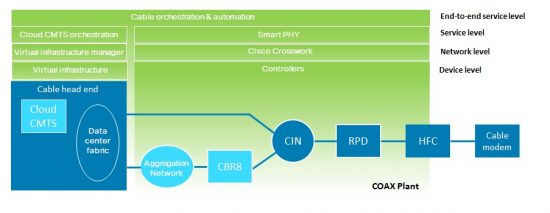
blog
The Cable Story, Part 4: Automating the Network
blog
Working remote? Use VoIP

blog
Edge and fog computing: Cutting through the haze (Part 1)

blog