blog
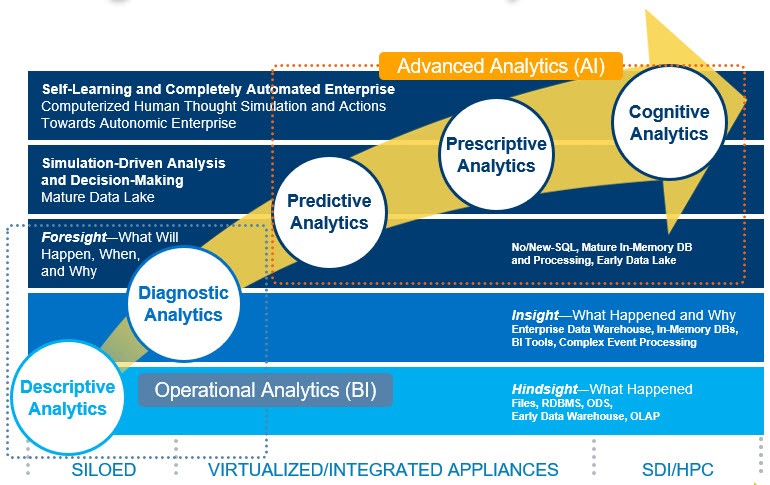
The Rise of Deep Learning in the Enterprise
blog
IT security policies your company needs
blog
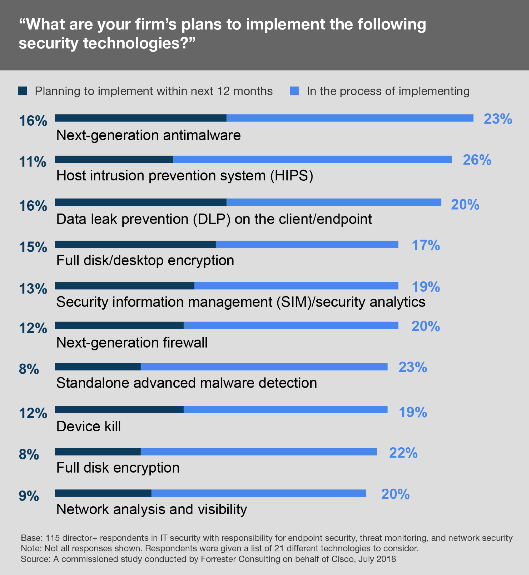
New Report Shows Correlating Network and Endpoint Data is Highly Manual
blog
4 BYOD security risks you should prepare for
blog
How business continuity plans can fail

blog
5 Most Common Application Performance Issues

blog
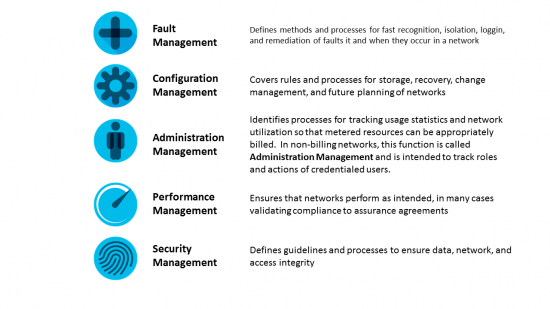
Machine Learning: Beyond the buzzword
blog
How Antifragile Systems of Trust Can Strengthen Blockchain Initiatives
blog
How to reduce your PC power consumption
blog