blog
What VoIP services can you choose from?
blog
6 Common ways virtualization fails
blog
Secure healthcare data from hackers
blog
3 Simple security tips to prevent data theft
blog
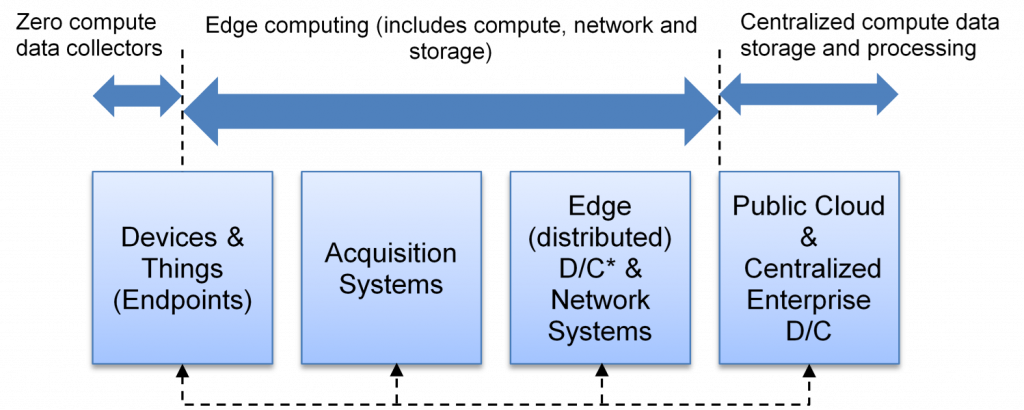
Understanding edge computing: A topology based taxonomy
blog
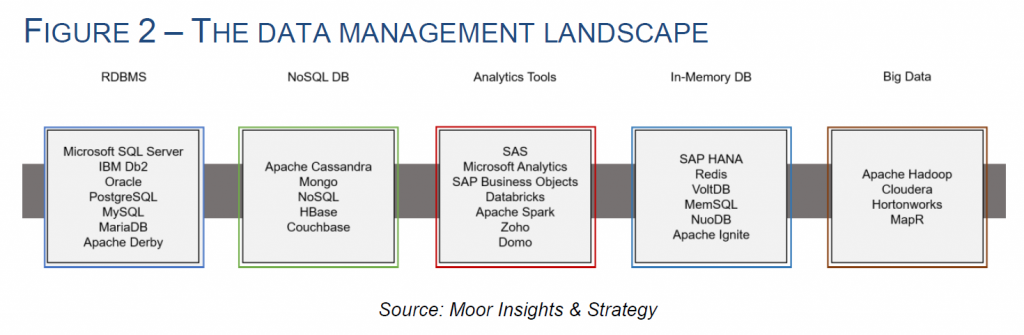
Is data the new crude oil?
blog
Cloud migration tips for unified communications
blog
Web hosting explained

blog
Scaling the collaboration experience

blog