blog
Learning password best practices
blog
The Heisenberg Principle of Security vs. Privacy
blog
Redefining data protection
blog
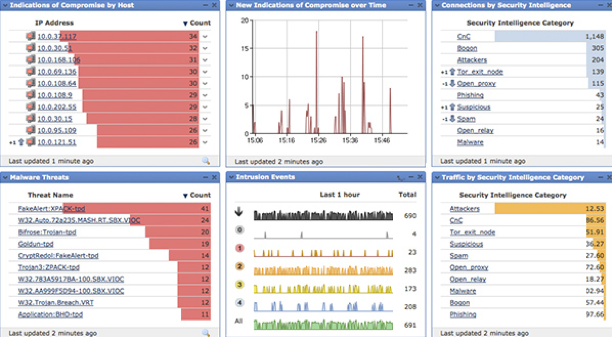
Layers of Security
blog
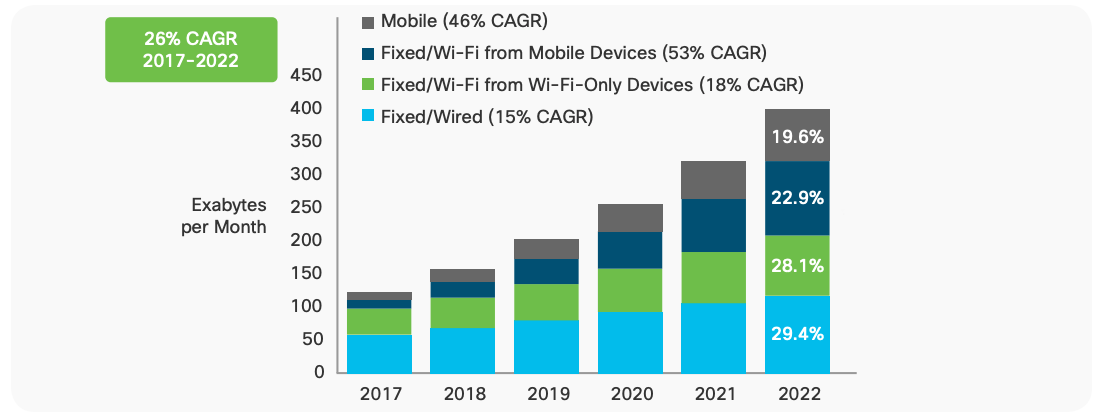
Why WiFi 6 and 5G are different: Physics, economics, and human behavior

blog
A guide to maximizing your chances of success with IoT

blog
Data lake vs. data leak
blog
Partner Post: 6 ways webex makes meetings experiences amazing

blog
The one-two punch of user and device trust
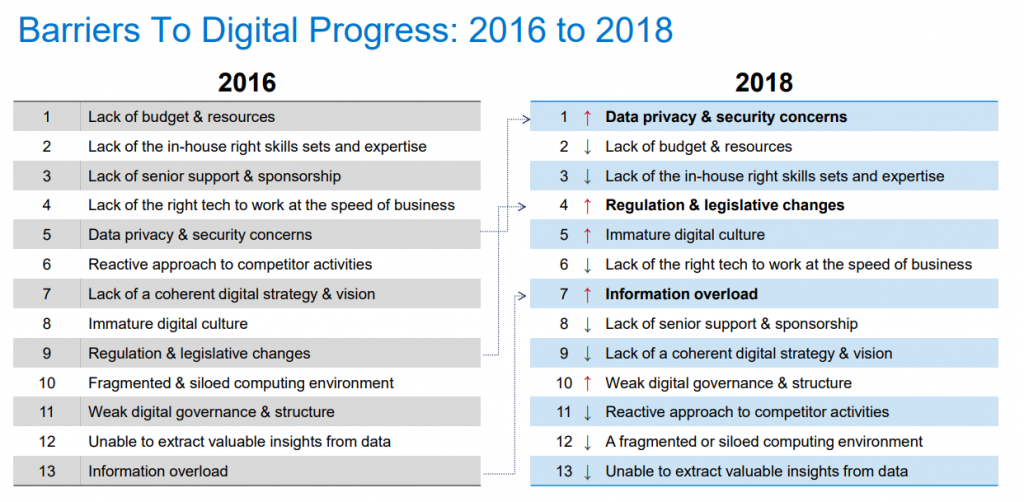
blog