
blog
VPNFilter: a global threat beyond routers
blog
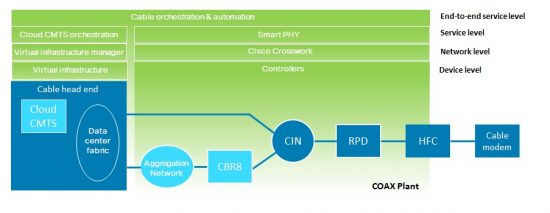
The Cable Story, Part 4: Automating the Network

blog
Edge and fog computing: Cutting through the haze (Part 1)

blog
The Cable Story, Part 2: Thoughts on How to Reinvent the Cable Network
blog
Data-Driven Hacks Part 2: How Can You Master the Past to Own the Future?
blog
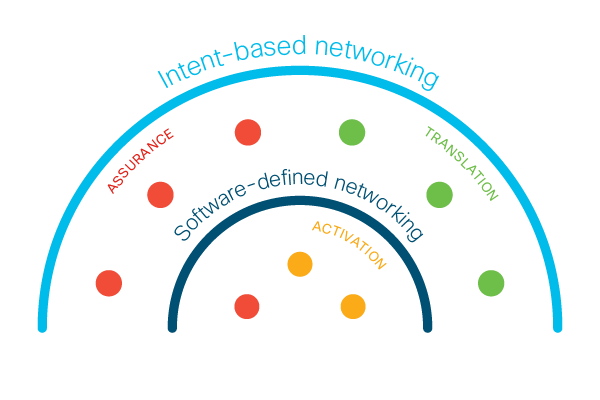
Why is intent-based networking good news for software-defined networking?
blog
A Primer on Jamming, Spoofing, and Electronic Interruption of a Drone
blog
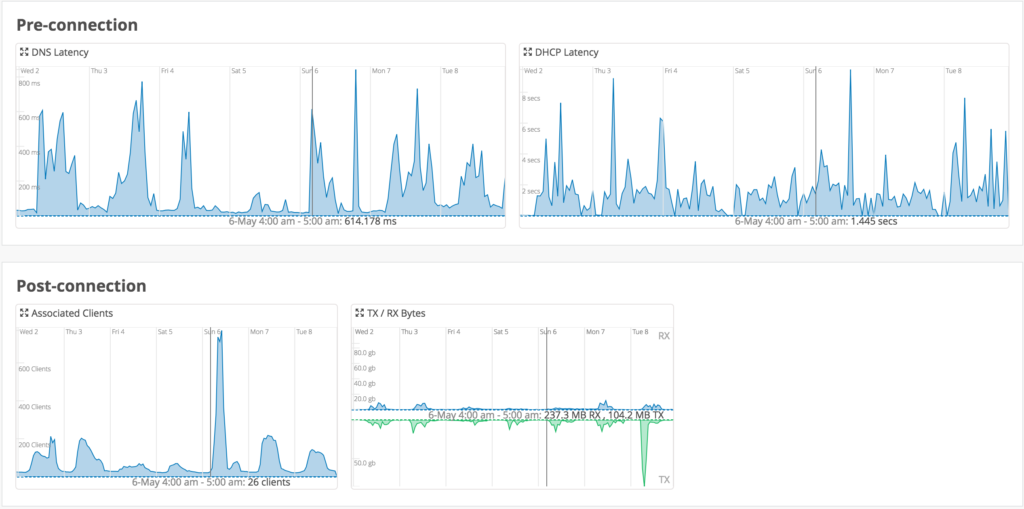
Mist Deployment (First Part)

blog
On-Prem vs. Public Cloud Deployments Differences & Similarities – DevOps Series

blog