
blog
In Pursuit of Invisibility: Fileless Malware

blog
Generation IoT: Transforming Disruption Into Opportunity

blog
An Open House Fiesta!
blog
3 Key Benefits of the WPA3 Wi-Fi Security

blog
Black Hat 2018: Securing the Expanding Cyberattack Landscape

blog
The Cost of Downtime in Multicloud IT
blog
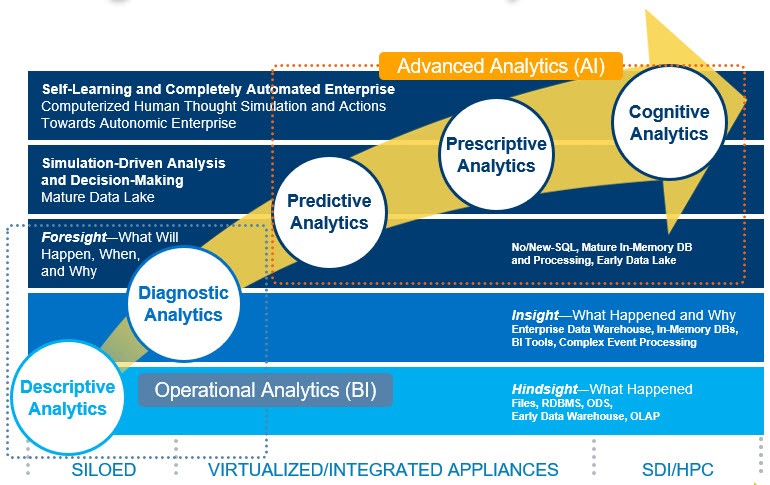
The Rise of Deep Learning in the Enterprise
blog
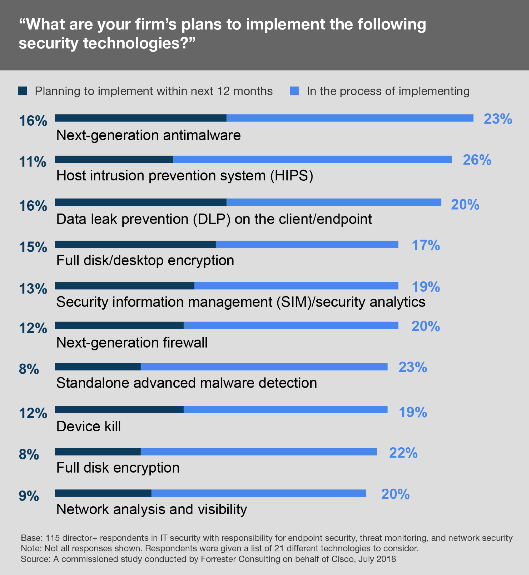
New Report Shows Correlating Network and Endpoint Data is Highly Manual

blog
5 Most Common Application Performance Issues

blog