Leveraging Cloud Environments for Security and Speed
The benefits and challenges of the new normal
In the Pacific Northwest, the weather, especially in the spring, can be pretty variable. Just look at this tweet from the National Weather Service in Seattle:
Living in Seattle, I can tell you with authority that cloudy days are the norm most of the year. But, we do not let variable weather or clouds stop us from enjoying the outdoors. We accept the clouds as the “norm” and we get on with our daily living – in my case, that means helping customers with their cloud strategy, or working with my colleagues to build exciting products and services.
Clouds are becoming more normal for organization’s IT environments as well. The movement of workloads from on-premises to public cloud continues to grow. We also see a move to private clouds, both on- and off-premises.
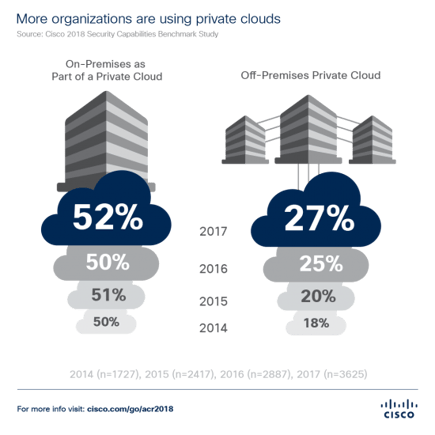
According to the Cisco 2018 Annual Cybersecurity Report’s(ACR) Security Capabilities Benchmark Study, the growth of off-premises private clouds continues unabated, up 50% since 2014 from 18 to 27%, while on-premises environments hold steady, yet grow to 52%.
Many enterprises want to take advantage of the new capabilities that have been brought to market in the last few years. For example, the trend to embrace and implement DevSecOps correlates to the availability of platforms to build and deploy into public or private clouds. According to the Cisco 2018 Security Capabilities Benchmark Study, 57% of respondents mentioned better data security as an important benefit from adopting cloud.
Cloud Service Providers (CSPs) are specialists, building infrastructure at Internet scale, with multitenancy designed from inception. They make the research and engineering investments to design, build and operate complex environments with high levels of service, rich interfaces for automation and orchestration, discrete billing mechanisms and relentless innovation.
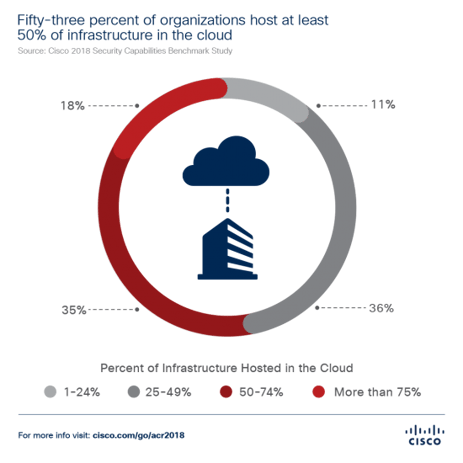
According to the Cisco 2018 Security Capabilities Benchmark Study, 53% of organizations that responded host at least 50% of their infrastructure in the Cloud.
While organizations are moving forward with cloud deployments, they are also cautious: according to the 2018 ACR, respondents indicated that securing data in the public cloud is one of the top three most challenging areas and functions to defend, along with mobile devices and user behavior.
Their caution is not surprising: While it’s easier to deploy new IT services, there may be impact to visibility and control mechanisms unless changes are made to the way security is implemented and managed. The security tools and processes that work for networks and data centers will not necessarily work in public clouds. We experience limits to visibility into the behavior of users, the disposition of data, and the network. Yet privacy and data must be protected, along with the ability to detect and respond to threats across cloud environments. Ideally, we should be able to achieve the same visibility and control for cloud applications and workloads that are available on the network behind firewalls. To accomplish this, it’s critical to adapt security processes, technologies, and knowledge of cloud environments.
To overcome these challenges and to achieve high adoption rates for cloud environments, it’s critical to develop a cloud security strategy to help identify the people, process and technologies that will be affected. The security strategy should broadly cover several areas:
- How do we integrate new applications with the legacy technology stacks?
- How do I ensure my teams have the right knowledge to leverage the investments in cloud we are making?
- How do we ensure that all the teams that need visibility have it, all the time?
- How do we account for our compliance and privacy obligations with our cloud-based applications and workloads?
- How do we respond to a breach that includes cloud-based resources?
- How do we maintain an accurate and dynamic understanding of where the organization’s datasets are located?
- How do we manage identities, entitlements and access controls?
Published with permission from blogs.cisco.com
